Active Directory is a directory service developed by Microsoft and used to manage Windows domain networks. Think about it like a phone book for Windows that’s used by 95% of Fortune 1000 companies. It stores information related to objects like computers or users and organizes those objects using a centrally controlled Domain Controller. Active Directory also provides user authentication using Kerberos tickets. It is the most commonly used identity management service in the world, and it can be exploited by abusing features and components without ever attacking patchable exploits.
Active Directory Components
Active Directory is made up of both physical and logical components. The main physical component is the Domain Controller, which hosts a copy of the AD DS directory store, provides authentication and authorization services, and allows administrative access to manage network resources, user accounts, groups, and security policies. Think of it like a big, centralized database that stores the information for every user, printer or other network device, and computers that make up the network. The Domain Controller is usually a centralized server, from which you can change passwords, add/delete users, and push security or group policies. The logical components include partitions, schemas, domains, domain trees, forests, sites, and organizational units (OUs).
| PHYSICAL | LOGICAL |
|---|---|
| Data Store Domain Controllers Global Catalog Server Read-Only Domain Controller (RODC) | Partitions Schema Domains Domain trees Forests Sites Organizational Units (OUs) |
The AD DS Data Store contains the database files and processes that store and manage directory information for users, services, and applications. It consists of the NTDS.dit file, which is usually stored in the %SystemRoot%\NTDS folder on the domain controllers. This file can be used by hackers to gain valuable information about user credentials, user groups, domain members, and access rights. As such, it is only accessible through the domain controller processes and protocols.
The AD DS Schema is a sort of blueprint that defines every type of object that can be stored in the directory and enforces rules regarding the creation and configuration of those objects. It contains formal definitions for every object and attribute that can exist inside the domain. Class Objects is an object type that dictates what objects can be created in the directory, like users or computers, whereas Attribute Objects are bits of information that can be attached to an object, like a display name.
Domains, Trees, and Forests
Active Directory is organized by several layers or groups of data. The overarching umbrella group is called the domain. Domains are an administrative, authentication, and authorization boundary that allows the domain admin to limit user access to resources, apply policies to groups of objects, and replicate data between multiple domain controllers. Think of this as a logical group of network objects and devices, like printers, faxes, VoIP, computers, and users that all share the same, replicable database. For example, a large business using Active Directory might have different domains for each department that shares a database. Domains can be organized into trees. A domain tree is a collection of domains or domain trees that help limit access to users, computers, and devices within a standard directory schema, directory configuration, and logical structure. All domains in the tree share a contiguous namespace with the parent domain, can have additional child domains, and create a two-way transitive trust with other domains.
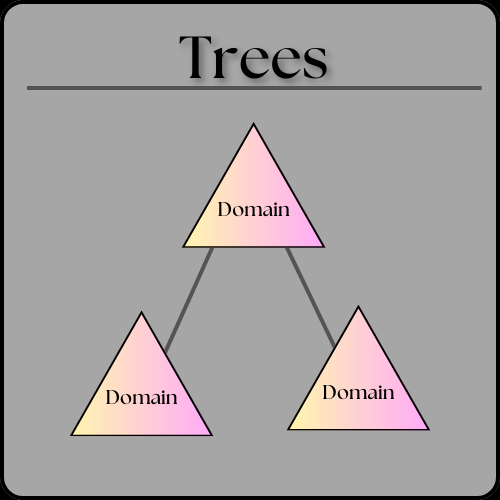
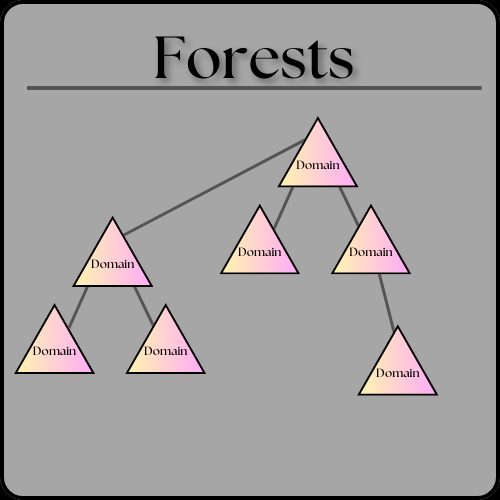
A collection of one or more domain trees is fittingly called a forest. Each tree in the forest shares a common schema, configuration partition, and global catalog for searching. They also share the Enterprise Admins and the Schema Admins groups. Forests provide a way to enable trust between all domains within the forest. The forest is the top of the structure. Active Directory breaks objects into Organizational Units (OUs) OUs are containers that contain users, groups, computers, etc. Organizational units represent the organization hierarchically and logically and can be used to delegate permissions to administer groups of objects, apply group policies, and manage collections of objects in a consistent way.
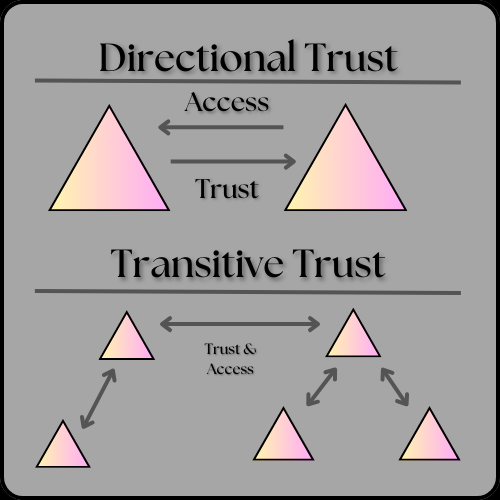
I briefly mentioned trusts in the context of domain trees. Trusts provide a mechanism for users to gain access to resources in another domain. For example, say you are in the account department but need access to the shipping database. Trusts allow individual user permissions to be adjusted based on their role or company need. Trusts can be Directional, which is when the trust direction flows from one trusting domain to another trusting domain, or Transitive, in which the trust relationship is extended beyond a two-domain trust to include other trusted domains. Think of trusts like a firewall or access control list deciding who gets access to resources and who doesn’t. All domains in a forest trust other domains in the forest, though trusts can extend outside the forest.
Objects
Objects are the basic building blocks that make up the active directory database. Examples of objects in the user, contacts, groups, computers, and printers. The following is a list of objects in a directory.
User – Enables network resource access for a user
InetOrgPerson – Similar to a user account; used for compatibility with other directory services
Contacts – Used primarily to assign e-mail addresses to external users; does not enable network access
Groups – Used to simplify the administration of access control
Computers – Enables authentication and auditing of a computer access to resources
Printers – Used to simplify the process of locating and connecting to printers
Shared folders – Enables users to search for shared folders based on properties
Final Thoughts
Active Directory uses LDAP, DNS, and Kerberos. Given that 95% of all Fortune 1000 companies use Active Directory, knowing how AD works is imperative when learning to exploit those features. As I mentioned, when we attack Active Directory, we do not need to take advantage of any exploits or malware, but rather, we can exploit the basic functionality to obtain user, admin, or domain controller credentials.
In the next post, we will talk about setting up a home lab to test various attack vectors. Learning to attack Active Directory is a vital skill for pentesters in 2025. Its also necessary to pass the OSCP exam, which is the gold standard for hacking certifications.!
![[+] – zer0space.html – [+]](http://zer0space.me/wp-content/uploads/2025/04/zzz.png)