
—Overview—
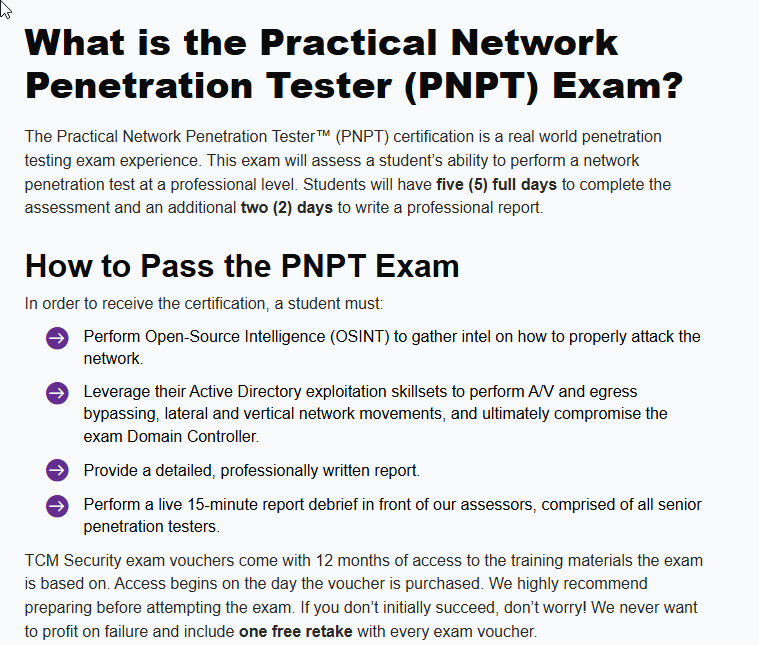
Recently, I took and passed the Practical Network Penetration Tester (PNPT) certification exam from TCM Security, which is sort of the next level up from the PJPT. The PNPT is an intermediate level ethical hacking certification that tests your skills in Active Directory, OSINT, login brute forcing, password guessing, lateral movement, pivoting, and privilege escalation.
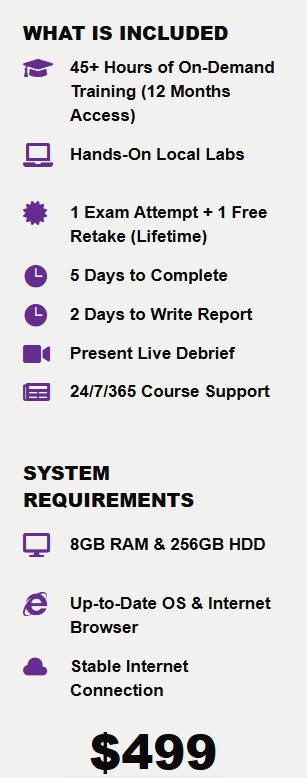
The $499 price is hefty, but still low for a professional certification. Included in that price tag is one free retake valid for a lifetime as well as almost 50 hours of training material with 12 months of access. The PNPT bundle includes 5 courses total with clear, concise, step-by-step instructional videos that are easy to follow for some hands on experience. The courses include:
- Practical Ethical Hacking – The Complete Course
- External Pentest Playbook
- OSINT Fundamentals
- Windows Privilege Escalation
- Linux Privilege Escalation
The Practical Ethical Hacking (PEH) course is the same PEH course from the PJPT, so I had a bit of an advantage in that I only had 4 more courses to make it through. I think there’s also some free courses included with the TCM Academy, including a course on soft skills for the job market that goes over resume tips, interviewing strategies, and some other non technical skills to land a pentesting role.
Unlike the PJPT, which does not expire, this certification expires 3 years from the certification date. Once you begin the exam, you will have 5 days to fully compromise an AD domain plus an additional 2 days to write a professional pentest report, after which you will have a 15 minute live debrief with TCM staff on camera where you will present your results.
—Training Materials—
As previously mentioned, the PNPT includes 5 different courses for study material. Each course includes several hours of clear instructional videos to follow along with, as well as several capstone exercises that will test the skill you learned in the course.
- Practical Ethical Hacking – The Complete Course: This is the same PEH course used for the PJPT. It provides a broad overview of ethical hacking skills and methodologies from basic bind shells and reverse shells to Active Directory enumeration and attacks to post exploitation and basic web application vulnerabilities. One thing I love about this course is its use of hands-on study materials. After the non-Active Directory portion, there’s about 5 vulnerable virtual machines complete with walkthroughs from the initial attack to gaining full root access. The Active Directory portion starts with a walkthrough for setting up an AD home lab with a domain controller and two workstations so that you can follow along with the videos. The web application portion also includes a local web server to test out vulnerabilities, as well as walkthroughs for each attack. Its a very thorough course and I’d recommend any aspiring hacker take this course.
2. External Pentest Playbook: This course will teach you how to go about attacking a network from the outside rather than starting from within the target subnet. While there’s not as much hands on lab work in this course, it does provide a lot of valuable information on password guessing/finding techniques, attacking login portals, privilege escalation, report writing, and even some common pentest findings. This course was very helpful for the exam.
3. OSINT Fundamentals: As the name suggests, this course covers the fundamentals of open source intelligence (OSINT) gathering. Whether you’re looking for information on a business, an image, email addresses, usernames, websites, passwords, or people, this course provides a ton of resources to gather any type of information you might need. This course also covers the intelligence lifecycle, OSINT automation, and OSINT report writing and wraps up with some fun OSINT challenges.
4. Windows Privilege Escalation: This course covers a broad range of privilege escalation techniques for the Windows OS. Some of the escalation paths include DLL hijacking, kernel exploits, password mining, port forwarding, RunAs, service permissions, startup applications, getsystem, executable files, registry, impersonation and potato attacks. The course also includes access to a Windows PrivEsc room on TryHackMe.com so you can follow along and try each exploit.
5. Linux Privilege Escalation: As you may imagine, this course covers some privilege escalation techniques for Linux. Some of the escalation paths include capabilities, docker, NFS root squashing, SUID escalation, kernel exploits, scheduled tasks, sudo exploits, and some automated tools for privilege escalation and exploitation.
—Exam—
The PNPT exam was a lot of fun… and a lot of frustration. You have 5 days to attack and fully compromise an Active Directory domain from outside of the network, starting with an OSINT investigation to discover a way into the internal network. The exam will test your ability to brute force using burpsuite, password guessing techniques from the course material, pivoting using something like sshuttle or proxychains, and Active Directory enumeration and attack skills, as well as critical thinking and attention to detail.
To be completely open and honest, I failed the exam 3 times, all of which were because I was thinking WAY too hard about it. I failed the first exam without breaching a single account. That was rough. On the second attempt, I managed to breach through the external network and set up a tunnel, but I assumed some things about usernames that were wildly inaccurate. I did manage to gain access to the internal network and move laterally, but then I got stuck on a particular machine. That’s what caused my second failure. Its also what caused my third failure, which happened when I gave up halfway through after being stuck in the same spot that I got stuck on for the previous attempt. It. Was. Frustrating.
Fortunately TCM offers any further retakes for $100, so you don’t have to break the bank to pass. “We never want to profit on failure,” the website says. That is an amazing business model, in my opinion. Too many companies are too focused on making a profit and lose sight of what’s actually important.
What makes this exam great is the fact that it is meant to mimic a real world penetration test with absolutely no flags to capture. The exam material consistently tells you to think of it like a real penetration test rather than a CTF, a sentiment I absolutely support. Enumeration is key here. If you are stuck, Enumerate Enumerate Enumerate!
The exam isn’t proctored or anything, but after 5 days the exam environment will close. Once I finally figured it out I realized I was only 10 minutes or so from compromising the entire domain. I was too busy focusing on what I should be that I was overlooking what I actually found.
Aside from the frustration, this was a lot of fun!
—Tips & Tricks—
The exam is not difficult, but it can be frustrating. Once you finally compromise the domain controller, though, the feeling is worth every metaphorical hair pulled from my head. I made so many assumptions and forgot the actual course material, which means I was thinking WAY too hard about some things. Here are my tips for setting yourself up for success on this exam:
- As always, be sure to get lots of sleep the night before your exam and eat something the morning of.
- Take as many breaks as you need. It feels counter intuitive, but taking a step away from your computer can help you see the problem more clearly and give you a broader perspective. Sometimes when we focus on the pixels, we lose sight of the actual image.
- I know it gets old to hear this, but everything you need is in the course materials, mostly the PEH, External Pentest Playbook, and OSINT Fundamentals.
- Read everything you find in detail. Look through every file and folder you have access to.
- Think of it like a real penetration test rather than a CTF or test question.
- The test is not made artificially difficult, but it is challenging.
- Check out the TryHackMe.com rooms Wreath and Holo to get an idea what the exam is like
- When writing the report, make sure you have a screenshot of every single step towards compromise.
- If you get stuck, take a break and look at the information you have. For any credentials, ask yourself what you can access with those credentials.
- Again, everything you need to pass the exam is in the course material.
Good luck, and happy hacking!

![[+] – zer0space.html – [+]](http://zer0space.me/wp-content/uploads/2025/04/zzz.png)