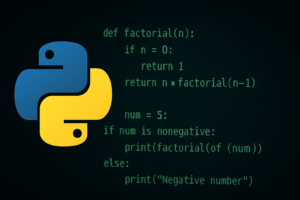
INTRO TO PYTHON Python is one of the most popular and beginner friendly programming languages in the world. For starters, a vast majority of pentesting tools you will find on GitHub are written in python. Whether you’re hoping to automate boring tasks, scrape and analyze data, or start building and customizing your own tools, Python […]
![[+] – zer0space.html – [+]](http://zer0space.me/wp-content/uploads/2025/04/zzz.png)