Ethical hacking, also known as penetration testing, is a controlled simulation of a cybersecurity attack with the intent of identifying weaknesses in a client’s network security posture. Companies will hire an ethical hacker to penetrate their network so test their security practices, password policies, and even staff procedures, after which they will submit a report of all findings along with remediation (how to fix it) for each finding. The goal is to strengthen the overall security posture by simulating an attack and identifying vulnerabilities before a malicious actor can exploit those vulnerabilities.
An internal penetration test is done from inside the network. This will usually be a VPN provided by the client or a laptop connected to the internal network provided by the penetration tester. Internal penetration tests simulate an attacker who has already breached the external network and demonstrates what a malicious attacker can do from inside the network. Conversely, an external penetration test is done from outside the network. The ethical hacker will simulate a remote attack, usually by first breaching some web application or login screen to gain a foothold into the internal network. There’s also a physical penetration test, in which the ethical hacker will attempt to penetrate the physical building where the client operates. This is a great way to test the effectiveness of external barriers, like RFID scanners, fences, security cameras, and any other means of external security.
The 5 Stages of Ethical Hacking
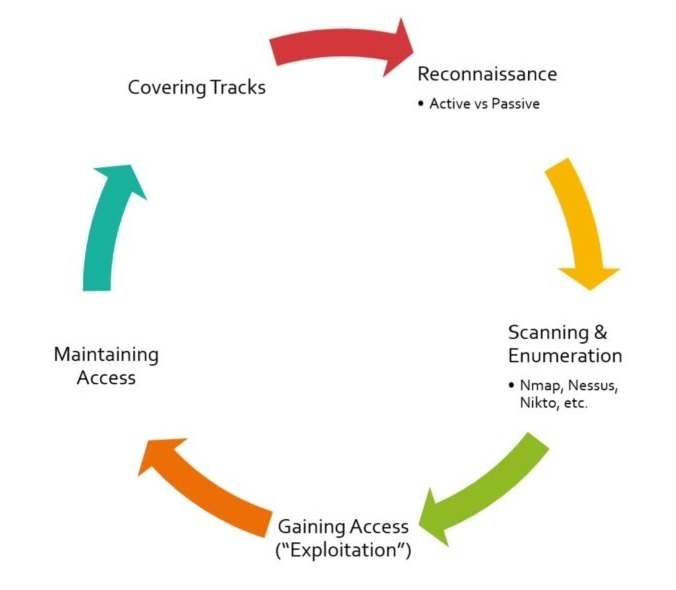
Stage 1: Reconnaissance
This stage is all about gathering information on your target to look for a foothold into the network. There are two types of reconnaissance, active and passive.
Passive reconnaissance involves using publicly available resources to gather as much information as possible, also called Open Source Intelligence (OSINT). Some examples of passive reconnaissance would social media sites like Twitter, Facebook, LinkedIn, Google, whois data if attacking a website, etc. Look for company pages, employee facebook pages, LinkedIn connections, an image posted by an employee showing their badge numbers, etc. You can also look for nearby restaurants or food trucks or anywhere employees gather for breaks. The main thing here is that this is all passive, meaning there is no actual interaction with the target network.
Active reconnaissance involves interacting with the target network. Social engineering would fit into this category as well.
Stage 2: Scanning & Enumeration
After gathering enough information on the client, its time to scan the target network for open ports and protocols, and checking for known vulnerabilities that can be exploited. Nmap, Nessus, and Nikto would fit into this stage. The goal is to find any way to gain remote code execution or some other access to the internal network.
Stage 3: Gaining Access (“Exploitation”)
Once enough information is gathered, the ethical hacker will run any exploits previously discovered in an attempt to gain access. There are countless ways this can happen, such as SQL injection, remote code execution (RCE), cross-site scripting (XSS), cracking login portals or password hashes discovered in reconnaissance phase.
Stage 4: Maintain Access
After gaining access, it is important to establish some kind of persistence within the network. Passwords get changed, user accounts get added/removed, networks get disconnected, etc. Its important to ensure you have access through any and all of that. If the cybersecurity team discovers that one of their accounts have been breached, disabling that account would effectively lock you out of the network, which means you need to search for another vulnerability to exploit and regain access. Some examples here would be a backdoor, malware, rootkit, privilege escalation, or even adding new users under your control.
Stage 5: Covering Tracks
Once the assessment has completed, this is the time to cover up/delete any indication that you were there. Remove any malware or rootkits installed, delete any logs or accounts created, and essentially return the network to the way it was when you started.
Ethical hackers are vital for any business with sensitive information across networked computers. Whether its a Fortune 500 company or a small therapy practice, ethical hackers can help companies comply with industry standards, maintain HIPAA compliance, protect private information and data, and ensuring that companies are up to date with the newest vulnerabilities and exploits. After the penetration test, it is important to get retested after 90 days or so to give the company time to fix the pentest findings. This second test will ensure all security vulnerabilities have been patched, all security practices and procedures have been updates, and overall security posture has improved.
Ethical hacking is a great way to test how employees, security policies, password policies, and other network security procedures will hold up to a malicious attacker. A penetration test is almost like a vaccine, providing a small dose of a malicious network attack to strengthen the organization’s overall security posture.
![[+] – zer0space.html – [+]](http://zer0space.me/wp-content/uploads/2025/04/zzz.png)